Businesses face constant threats from cybercriminals looking to exploit vulnerabilities and access sensitive information. One of the most effective ways to safeguard your organisation is through penetration testing. This process simulates real-world cyber attacks, or ethical hacking, to identify and address weaknesses in your IT infrastructure.
In this blog post, we will introduce penetration testing and explain how testing across the 7 layers of IT security provides a comprehensive understanding of your security landscape.
What is Penetration Testing?
Penetration testing, often referred to as "pen testing," involves simulating cyber attacks “ethical hacking” on your computer systems, applications, and networks to uncover vulnerabilities before real hackers can exploit them. This proactive approach allows organisations to understand their security posture and take necessary actions to mitigate risks. Penetration testing is not just about identifying vulnerabilities but also about understanding how these weaknesses could be exploited and the potential impact on the business.
Introducing the 7 Layers of IT Security
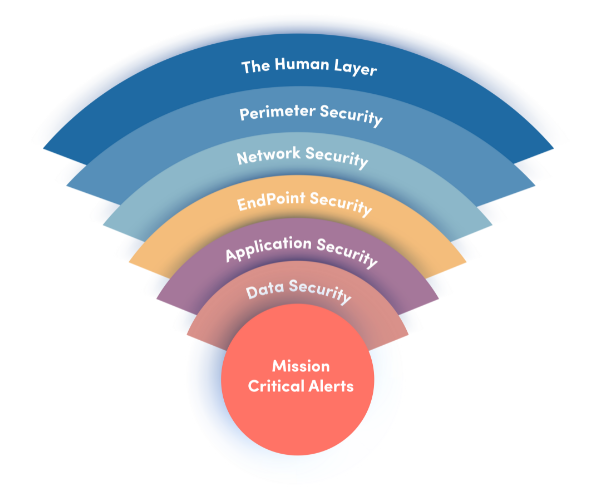
To fully understand and secure your IT environment, you must consider the following 7 layers of IT security, starting from your biggest exposures.
- The Human Layer: Measures that address the security threats posed by human actions, including phishing simulations and access management.
- Perimeter Security: physical security that protects the business premises, and logical security measures that protect access from the internet
- Network Security: Controls that protect an organisation’s internal network and restrict unauthorised access.
- Endpoint Security: Measures that secure the connection between devices and the network.
- Application Security: Security measures that protect access to applications and the internal security of those applications.
- Data Security: Controls that protect the storage and transfer of data.
- Mission Critical Assets: This layer focuses on the most important data and systems that your business needs to protect.
Why Testing These Layers with Penetration Testing is Essential
Penetration testing across these 7 layers provides a comprehensive understanding of your security landscape. Here’s why:
- The Human Layer:
Humans are often the weakest link in cybersecurity. Pen testers conduct phishing simulations and social engineering attacks to assess and improve employee awareness and response to potential threats. This helps mitigate risks posed by cybercriminals, malicious insiders, and negligent users. - Perimeter Security:
Perimeter security includes both physical and online security measures. Penetration testing evaluates these controls, ensuring they are effective in preventing unauthorised access to your business premises and evaluating your online exposure. This includes testing network perimeter firewalls, web applications, internet facing servers, anti-DDoS measures, and physical access controls. - Network Security:
Network security is crucial for preventing unauthorised access and data breaches. Pen testers simulate attacks on your network infrastructure by identifying and exploiting internal network vulnerabilities, testing intrusion detection and prevention systems, and identifying network segmentation configuration weaknesses. This helps you strengthen your network defences and limit potential breaches. - Endpoint Security:
Endpoints, such as laptops, desktops, and mobile devices, are common entry points for cyber attacks. Penetration testing assesses the security of these devices, ensuring they are protected against malware, unauthorised access, and other threats. Thus, it secures the connection between endpoints and your network. - Application Security:
Applications are often a primary target for attackers. Pen testers identify vulnerabilities within your applications, such as SQL injection, cross-site scripting (XSS), and improper access controls. By addressing these issues, you can prevent attackers from exploiting application weaknesses to gain access to sensitive data. - Data Security:
Testing data security controls ensures that your data is secure during storage and transfer. Pen testers evaluate encryption methods, data storage solutions, and data transfer protocols, identifying any weaknesses that could be exploited to access or corrupt data. - Mission Critical Assets:
Penetration testing identifies vulnerabilities that could lead to unauthorised access to your most critical data. By simulating attacks, you can understand how an attacker might exploit weaknesses to access mission-critical assets, allowing you to implement appropriate security measures to mitigate cyber threats.
Penetration testing identifies vulnerabilities that could lead to unauthorised access to your most critical data. By simulating attacks, you can understand how an attacker might exploit weaknesses to access mission-critical assets, allowing you to implement appropriate security measures to mitigate cyber threats.
By conducting penetration testing across all 7 layers of IT security, you gain a comprehensive understanding of your security landscape. This holistic approach allows you to identify and address vulnerabilities at every level, ensuring robust protection for your organisation’s mission-critical assets. Regular penetration testing not only enhances your security posture but also demonstrates a proactive commitment to cybersecurity, which is essential for maintaining trust with customers, partners, and stakeholders.
