Australian Cyber Security Centre (ACSC) Alerts
The following vulnerabilities have been listed on the ACSC site as high alerts.
Want to know more?
Speak To An ExpertThe cyber security landscape
Reports from the ACSC and the ACCC are telling us that Australian businesses are more vulnerable ever. Now is the time to act.
300 million
Estimated annual losses to cybercrime
1 in 5
1 in 5 SMBs did not know the term “phishing"
59%
Users who use the same password for all accounts
144 Reports
of cybercrime received by the ACSC per day
After extensive research and collaboration with leading international cybersecurity vendors, our security team created a range of solutions based on global best practices for small, medium and enterprise organisations. Our comprehensive experience with real-world cybersecurity incidents has also helped shape our service offerings.
Emerging IT Cybersecurity provides an end-to-end solution from the outside in through a six-layered approach that aligns our cybersecurity solutions to an organisation’s business strategy and mission.
Our solution is broken down into the six most critical components that should be addressed when developing a cybersecurity plan to improve your organisation’s IT security posture.
These include Operational Security, User Education and Awareness, Network Security, Application and OS Security, Information Security and Data Recovery/Data Continuity.
I Want To Talk
Australian Cyber Security Services Supported 100% in Australia.
Not all Cyber Security services are made the same. When signing on with Emerging IT cyber security services you work with an expert right here in Australia.
The benefits of having cyber security services from Emerging IT
Collaborative strategy
We work with you to create your cyber security strategy by analysing and incorporating your data, goals and people with our expertise, helping your business grow sustainably and securely.
Clarity
We invest in training, research, and education not only so we can provide the most sophisticated cyber security solutions, but also so we can offer the best guidance to our customers.
Future safeguarding
Together, we are always prepared. We work collaboratively with you to ensure that your critical data is protected, your employees are educated, and your business is safeguarded for the future.
Data-driven decision making
We use your business data to discover vulnerabilities in your network. Once they’re identified, we help you build a plan around protecting your data and preparing for what's next.
Australian Always
All of our employees are Melbourne or Sydney based, so when you call up about a cyber security concern, you speak to a local expert who cares about protecting your business.
Things to consider when choosing a Cyber Security Partner
Custom Solution
Cyber security solutions like all solutions need to solve a problem and aren't a one size fits all. Your security partner should assess vulnerabilities in your business and help you mitigate the risk.
Nine-To-Five
Some partners only offer standard business hours. Unfortunately, cybercriminals do not work these hours. Ensure your provider has the ability to work around the clock.
Location, Location, Location
Shifting your business data to the cloud? Without the right checks, your data could find itself in an overseas data centre. Your security partner should be trusted to be involved in all ICT related matters.
Don't Skimp On The Audit.
Not doing an audit might mean you save some money. However, your new partner will find it challenging to understand business vulnerabilities and help mitigate them.
Meet and Greet
More than likely, your security partner will have a dedicated security team onboard. Ask to meet them. They should be knowledgable and be able to discuss the latest threats.
Ready to talk Cyber Security?
CONTACT USYour Cyber Security Journey
These security services provide an end-to-end holistic solution that protects your critical data through our multi-layered approach. This unique approach is tailored to align with your own unique business strategy and mission.
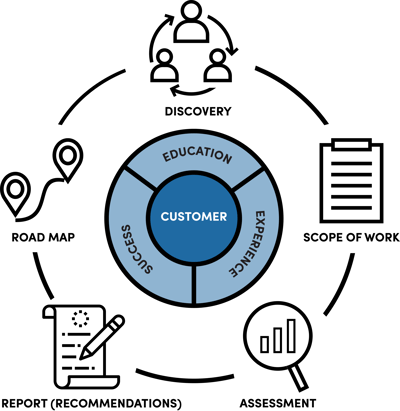
Cyber Security Assessments
The best way to understand your cybersecurity needs is to get an assessment.
We offer business grade security assessments to help your organisation identify vulnerabilities
within your business operations and corporate network.
We offer the following cybersecurity assessments:
Essential Eight Audit
Based on the Australian Cyber Security Centre's (ACSC) essential eight maturity level framework, the Essential Eight Audit is designed to align your business with these strategies and strengthen your overall security posture.
Penetration Testing
Our Penetration Testing services include External and Internal testing, Web Application and Internet Facing Infrastructure Penetration Tests, Active Directory and Wireless Network Penetration Tests, Social Engineering, Audits, bundles & customised tests.
Want To Learn More About Our Assessments?
Get Started hereUser Awareness Training
Social engineering and phishing attacks appear in many forms. However, they ultimately have a similar goal to steal money or essential information about a person or company.
Our User Awareness Training empowers your employees through constant security awareness training, creating human firewalls and a proper defence against cybercrime.
Ready to get started?
Learn More About User Awareness TrainingNetwork Security
Accompanied by User Awareness Training, Every business should have ongoing basic network security to reduce the risk of a cyber attack on their business. You can pick and choose your Managed Products or create a bundle.
Want A Managed Security Service That Works?
Find Out More HEreEmerging IT Essential Eight Maturity
These strategies include application control, patch applications, user application hardening, patch operating systems, restrict administrative privileges, multi-factor authentication (MFA), daily backups and configure Microsoft office macro settings.
Our security division, guided by the ACSC, has developed a maturity level framework designed to simplify these strategies so that your business can plan for next-generation cyber security threats that are affecting business today.
Essential Eight Strategies

Application
Control
Application control to prevent the execution of unapproved & malicious programs
Patch
Applications
Patch computers with critical vulnerabilities and use the latest versions of applications

Configure Office macro settings
Configure Microsoft Office macro settings to block macros

User application hardening
Configure web browsers to block Flash and Java. Disable unnecessary features in applications
Restrict administrative access
Restrict administrative access to operating systems and applications based on user duties

Patch operating systems
Patch operating systems with critical vulnerabilities within 48 hours

Multi-factor authentication
Enforce multi-factor authentication for VPNs, RDP, SSH, and other remote access, and all users

Daily
backups
Daily backups of essential data and retained for at least three months
Ready to get started?
Learn more about Essential Eight MaturityCloud Security & Continuity

Cloud Security
All our cloud services come with best of breed technologies to ensure your data is as safe as possible. Secure physical and remote access, Multi-Factor Authentication, premium monitoring and alerting, and best practice configurations.
Cloud Backup
Our cloud backup solutions give you an air gap between your live data and company backed up data. In the event of a disaster, your backups remain behind an extra layer of security. See our Backup and Disaster Recovery page for more information.
Cloud Continuity
In addition to cloud backup, we offer business continuity services. Our tried and tested cloud continuity allows your business to be back up and running rapidly in the event of a disaster. This includes email, server and internet connection options.

Cloud Compliance
Moving your infrastructure and data to the cloud doesn't mean you relinquish your responsibility, it is paramount to ensure you meet compliance and governance requirements where they apply to your industry. We have options to suit.
Ready to future-proof your business?
Fill in the form below to request a quote.





.png)

.png)


.png)
.png)
.png)
.png)
.png)




